Detect DNS Spoofing, Protect Your Digital Identity
Use performance analytics to protect your site from the severe consequences of DNS spoofing and poisoning.
Your Domain Name is your digital identity, the first interaction your customers will have with your online brand.
In this article we will cover DNS Poisoning and why you need to proactively monitor and catch it before it affects your business; but before we get to testing and detecting a problem, let’s first define the problem.
So what is DNS Poisoning?
DNS Cache Poisoning is to DNS what identity theft is to a person. Anyone who has experienced it knows how hard identity theft is to clean up, but the hardest part is detecting it in the first place.
– When a user tries to access any website/URL (ex : www.xyz.com), the first step is to convert the Domain Name to an IP address.
– If the computer does not already have the information, it has to connect to a DNS (Domain Name System) server that can provide the information. Usually it is your ISP’s DNS Server, unless you have manually set your computer to use another DNS Server such as GOOGLE DNS.
– If the ISP’s DNS server does not have the information, then it goes to the next level, which is the Root Server. The Root Server then points you to the GTLD Server, which will have the information of all the (.com) domains. This will finally point you to the Authoritative Name Servers of www.xyz.com.
– This server will respond with the numerical IP address of the domain www.xyz.com
– All the different servers that were part of this process will cache the response they received and forward the details to the requesting computer/server.
– In the above process, the information has to pass through a number of routers and servers. Each one of those steps is a weak link. If one of those servers is compromised it will tamper with and poison the results.
– Your computer will then connect to this IP address and ask for the content of www.xyz.com. However, the IP address is incorrect so either the website may not load or, in a worst-case scenario, you will be presented with a fake website that might compromise your computer and ultimately steal your personal information.
– If your DNS has been hijacked or compromised, this is not strictly a technical problem. Your entire company is at risk. The damage is far reaching as it impacts trust, brand value, and revenue.
Fortunately, DNS Poisoning can be prevented through proactive DNS testing. We have always recommended to have a strong monitoring strategy around DNS. As discussed above, DNS resolution is a complex bunch of recursive requests that goes through a number of levels of queries before it can direct the user to the actual IP address. It is very important to be able to detect the exact location of failure.
Catchpoint’s DNS Experience Test: The Best Cop to detect DNS poisoning
Catchpoint’s DNS Experience Test measures the time it takes to resolve the domain by emulating a DNS Resolver. It queries all the levels from the Root Server, TLD Server, Authoritative Name Server, etc.
If you are C-Naming your host to a CDN, then it will also test how long it takes to query all the different DNS servers of the CDN before returning the IP address of the server where the website content is hosted.
Example 1: Monitoring the DNS resolution flow of www.google.com from different geographies
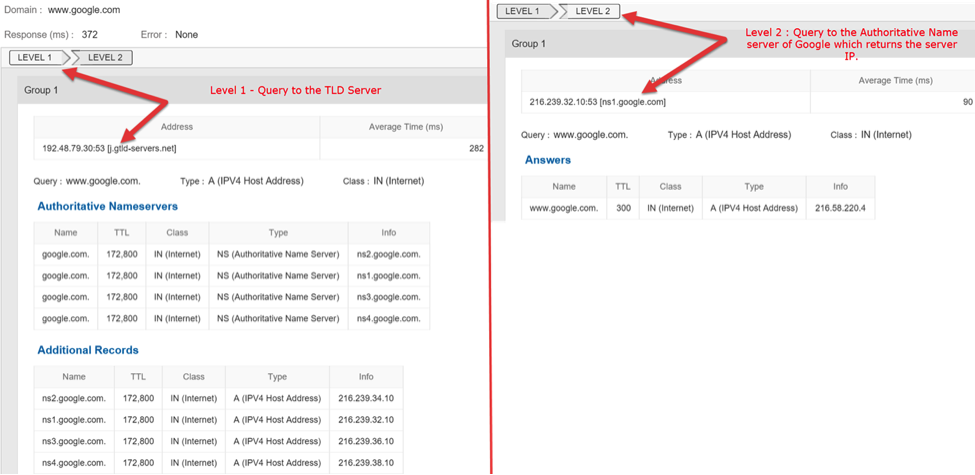
We can see the response below:
Example 2: Monitoring the DNS of a domain that is C-Named to a CDN and that has multiple levels of queries, which makes it even more complex.
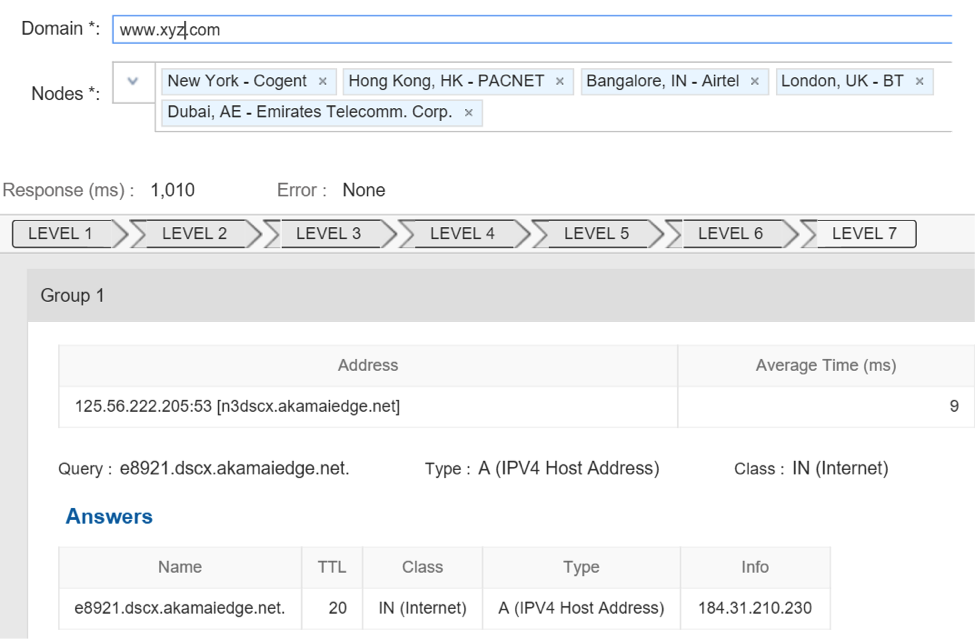
In the above two examples we can see how Catchpoint DNS Experience Test goes through every level and measures not just the availability and response of those DNS servers, but also validates if those DNS servers are returning the correct response.
This makes it easier to catch if you are vulnerable to DNS Cache Poisoning even before it affects your real users who are spread across the country/continent/world, or even other internet worlds such as China or Iran, where DNS hijacking is not only done by hackers, but by government agents.


