A BGP Guide for the non-Network Engineer
This blog focuses on the basics of BGP (Border Gateway Protocol) for the non-network engineer.
As part of the launch of our new DEM product, Network Insights, we recently ran a five-part blog series on BGP, providing engineers with detailed information on how BGP works. This blog focuses instead on the basics of BGP for the non-network engineer.
What is BGP?
Border Gateway Protocol (BGP) is the Internet’s primary routing protocol. It has been described as the protocol that “makes the Internet work” because it plays such an important role in allowing traffic to move quickly and efficiently.
The original function of BGP was to carry Internet reachability information between edge routers (it is sometimes described as a reachability protocol). It has since expanded to also carry routes for VPNs, IPv6, Multicast, and a range of other data. BGP provides network stability as it guarantees routers can rapidly adapt to send packets via a different connection if one Internet pathway goes down. It does this by exchanging routing information across the Internet, through the use of BGP-speaking routers and routing tables.
Internet routing is made up of two different types:
- Interior Gateway Protocols (IGP): used for routing within an autonomous system (AS), such as EIGRP, OSPFF and RIP
- Exterior Gateway Protocols (EGP): the Border Gateway Protocol is currently the de-facto standard EGP routing protocol used in inter-domain routing.
BGP was originally proposed as a stopgap solution to replace the existing EGP. Fast-forward thirty years, and it remains one of the central pillars of the Internet. We are currently on version 4 (BGP4 or BGP-4).
How Does BGP Work?
BGP specifies a TCP-based communications method to help autonomous systems exchange routing information over the Internet. An AS is a collection of routers run by a common administration, such as a large enterprise or university, which control a range of IP addresses. Each AS is assigned an Autonomous System Number (ASN).
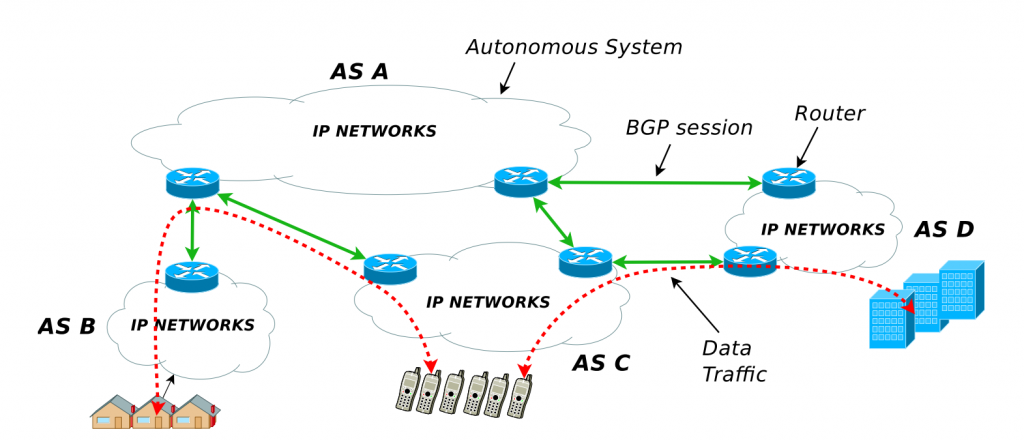
BGP determines routing decisions based on paths, rules, and/or network policies set by a network administrator. Each AS manages a routing table that contains every known route to other networks, which is then shared with neighboring networks, also known as peers. The BGP decision process enables the AS to select the most efficient route available by analyzing the path attributes of each candidate, applying a set of criteria (including weight, local preference, shortest AS Path, etc.). This means that BGP might direct traffic along one path to reach its destination and along a different path on its return trip, leading to asymmetric routing.

The focus of BGP design and implementation has always been security and scalability, making it more difficult to configure than other routing protocols; it is also more complex, making it one of the slowest converging routing protocols.
The Vulnerabilities Inherent in BGP
The very qualities that make BGP so successful also leave it extremely vulnerable to human error and malicious attack.
There is very little oversight of the large number of AS’s that comprise the modern Internet, and almost no oversight for how each configuration of each AS peering filter should happen. This makes is a highly flexible protocol; however, if a new, bogus route is announced, whether accidental or deliberate, traffic will be sent to the wrong network, and as we have seen recently, the problem can rapidly propagate across the rest of the net.
There are two main types of vulnerability:
BGP leaks – route leaks involve the unintentional creation of false routing information, thereby misdirecting traffic and leaving it vulnerable to misuse. Route leaks are usually the result of human error due to filter misconfiguration, leading to the illegitimate advertisement of prefixes and blocks of IP addresses, which spread across networks and result in suboptimal or incorrect routing.
BGP hijacking – route hijacking involves the deliberate takeover of collections of IP addresses through the corruption of Internet routing tables. If the injected announcement is more efficient than the real one, the traffic will be rerouted to the injected announcement. BGP hijacking is not always easy to detect as activity can be hidden behind other AS’s, or may involve the announcement of unused blocks of IP prefixes, which are unlikely to be noticed. As a result, Internet traffic can be sent the wrong way, covertly monitored, or intercepted. Spammers can also use BGP hijacking to spoof legitimate IPs and send users to bogus websites.

The Impact on End Users and Business
Both types of vulnerability leave the end-user subject to problems. These range from the inconvenient, such as slow page loading times due to traffic taking an unnecessarily long route to the highly serious, such as traffic interception or black holing of an entire network. This kind of attack can lead to the kind of blanket outages that we see with DDoS attacks. Attackers can also censor specific sources of information by only black holing specific networks.
The man-in-the-middle nature of rerouting also allows attackers to eavesdrop on certain parts of the communications, or even alter the traffic itself. They can redirect traffic from your legitimate site to malicious sites pretending to be part of your network. This can lead to the theft of sensitive information or credentials, or even delivery of corrupt malware. We saw this in action last year when hijackers attacked AWS’s DNS service to steal Bitcoin. Spammers can also damage the reputation of a business by abusing your ASN’s reputation to carry out spam runs.
While businesses can’t entirely prevent BGP misconfiguration or deliberate misuse of BGP, they can monitor what is going on. By monitoring the BGP routes that relate to your AS, you can gain visibility into any kind of BGP vulnerability that might be underway, and can carry out an incident response plan.
Our new product, Network Insights, is intended to close the visibility gap, offering IT teams real-time visibility into their digital services. Network Insights has four key capabilities, offering BGP, DNS, Traceroute, enterprise and endpoint monitoring, allowing you to view the network path from end to end.
Want to learn more about the Border Gateway Protocol? Download our new ebook, The Comprehensive Guide to BGP.


